Introducing CryptoLocker: The worst computer virus in 10 years
In September 2013, several antivirus and information security companies began noticing a new piece of malware that was spreading across the net.
Today, Australia is the 6th most targeted country in the world for ransomware with over 20 000 computers infected.
CryptoLocker is a ransomware trojan, a malware that restricts access to infected systems. It targets computers running Microsoft Windows and propagates via infected email attachments.
Once a computer is affected the malware then displays a message, which offers to decrypt the data if a payment is made by a stated deadline, and threatened to delete the private key if the deadline passes.

CryptoLocker basically keeps all the files on your PC under siege.
If the deadline for the payment is not met, the malware offers to decrypt data via an online service provided by the malware’s operators, for a significantly higher price in bitcoin.
Why CryptoLocker is dangerous to your business
CryptoLocker is different than most Malware because it can render files on a computer and potentially any server that computer has access to unusable.
It does this by encrypting certain types of files, documents, and databases with RSA/AES encryption, the same encryption used to protect banking information and other highly confidential data.
Once encrypted, programs like Microsoft Word and Adobe Reader can no longer read the files.
Because of the strength of these encryption types the encryption cannot be undone without the encryption key.
CryptoLocker then presents you with a popup window offering to undo the encryption for a sum of money if paid within a timeframe.
Here is a list of CryptoLocker symptoms to watch out for
Most or all of the files on your computer or on folders on your server will not open. You will be prompted with one of the following errors:
- A compatibility pack needs to be downloaded to understand the file.
- The file is not in the correct format or is corrupt.
- A popup appears with a ransom notice stating, “Your personal files are encrypted!”
CryptoLocker prevention tips
The best method of preventing your computers from becoming infected with CryptoLocker is to educate your staff.
Below are a few CryptoLocker specific security recommendations that you can e-mail to your staff:
- CryptoLocker is spread mainly through e-mail attachments in e-mails that are altered to look like they are coming from common business vendors and resources like: Australia Post and even government agencies. Be cautious about opening attachments in unsolicited e-mails from these sources, and if necessary, put in a call or e-mail to the source in question to confirm that the e-mail is safe.
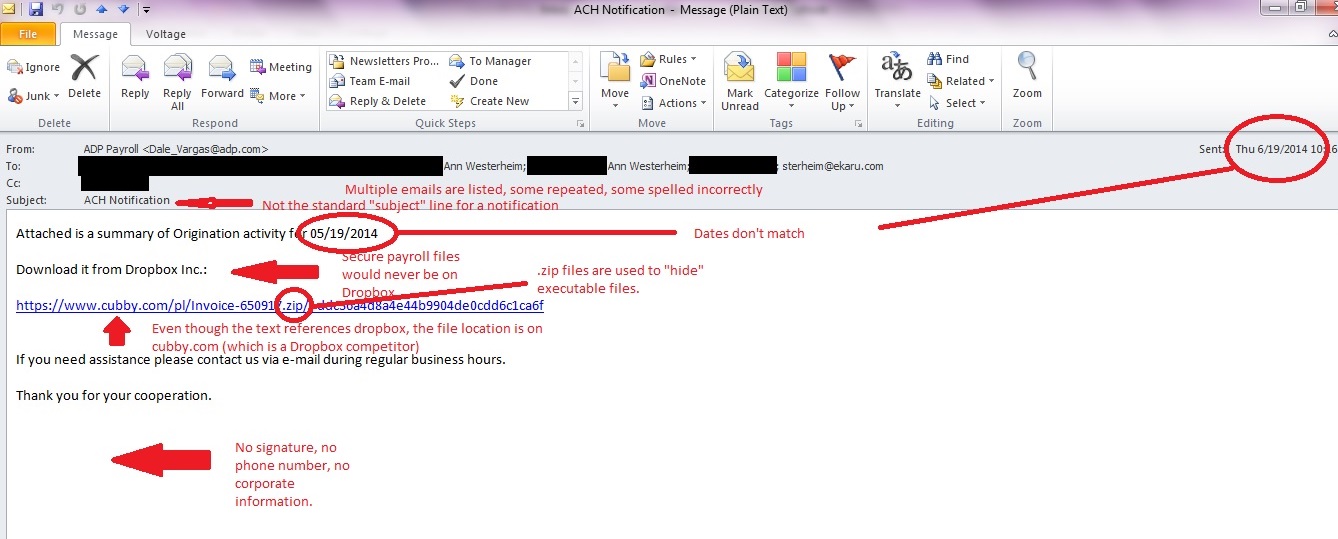
- If you are not expecting an e-mail from the sender or do not recognise the sender, be cautious about opening attachments or clicking on links in the e-mail.
- If you are unsure about an e-mail, involve Technical Support Desk personnel before opening any attachments or clicking any links contained within.
- Try to avoid browsing internet sites that are not necessary for your day to day work as these could contain hacked advertisements and links.
- Being particularly wary of emails from senders you don’t know, especially those with attached files.
- Disabling hidden file extensions in Windows will also help recognise this type of attack.
Conclusion
Having a backup system in place for your most valuable files is vitally important to avoid CryptoLockers!
This will help mitigate the damage caused not only by malware infections, but hardware problems or any other incidents as well.
We advise you to take precautions when opening emails and to ensure good backups of any data are kept offline.








Comments
No comment yet.